Thursday Feb 26, 2026
Thursday Feb 26, 2026
Wednesday, 26 July 2017 00:00 - - {{hitsCtrl.values.hits}}
The Cisco 2017 Midyear Cybersecurity Report (MCR) released on Monday uncovers the rapid evolution of threats and the increasing magnitude of attacks, and forecasts potential ‘destruction of service’ (DeOS) attacks. These could eliminate organisations’ backups and safety nets, required to restore systems and data after an attack. Also, with the advent of the Internet of Things (IoT), key industries are bringing more operations online, increasing attack surfaces and the potential scale and impact of these threats.
Recent cyber incidents such as ‘WannaCry’ and ‘Nyetya’ show the rapid spread and wide impact of attacks that look like traditional ransomware, but are much more destructive. These events foreshadow what Cisco is calling destruction of service attacks, which can be far more damaging, leaving businesses with no way to recover.
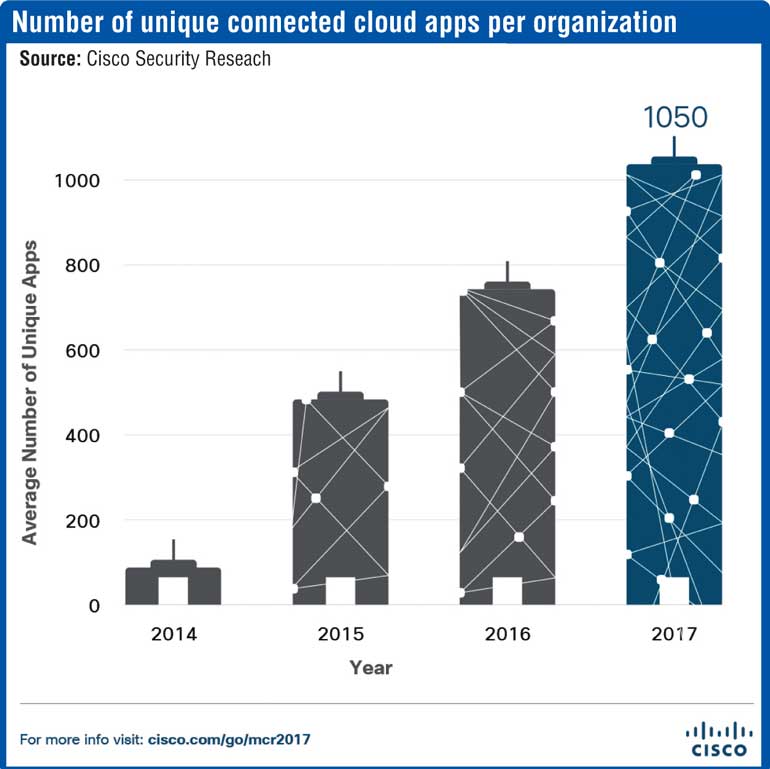
The Internet of Things continues to offer new opportunities for cybercriminals, and its security weaknesses, ripe for exploitation, will play a central role in enabling these campaigns with escalating impact. Recent IoT botnet activity already suggests that some attackers may be laying the foundation for a wide-reaching, high-impact cyber-threat event that could potentially disrupt the Internet itself.
“As recent incidents like WannaCry and Netya illustrate, our adversaries are becoming more and more creative in how they architect their attacks. While the majority of organisations took steps to improve security following a breach, businesses across industries are in a constant race against the attackers. Security effectiveness starts with closing the obvious gaps and making security a business priority,”said Cisco Vice President and Chief Information Security Officer Steve Martino.
Measuring effectiveness of security practices in the face of these attacks is critical. Cisco tracks progress in reducing ‘time to detection’ (TTD), the window of time between a compromise and the detection of a threat. Faster time to detection is critical to constrain attackers’ operational space and minimise damage from intrusions. Since November 2015, Cisco decreased its median time-to-detection (TTD) from just over 39 hours to about 3.5 hours for the period from November 2016 to May 2017. This figure is based on opt-in telemetry gathered from Cisco security products deployed worldwide.
“Complexity continues to hinder many organisations’ security efforts. It’s obvious that the years of investing in point products that can’t integrate is creating huge opportunities for attackers who can easily identify overlooked vulnerabilities or gaps in security efforts. To effectively reduce Time to Detection and limit the impact of an attack, the industry must move to a more integrated, architectural approach that increases visibility and manageability, empowering security teams to close gaps,” said Scott Manson, Cyber Security Leader for Middle East and Turkey, Cisco.
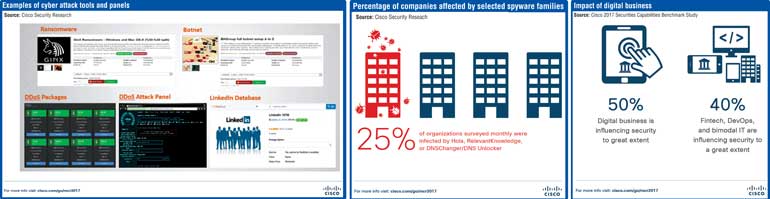
Cisco security researchers watched the evolution of malware during the first half of 2017 and identified shifts in how adversaries are tailoring their delivery, obfuscation and evasion techniques. Specifically, Cisco saw they increasingly require victims to activate threats by clicking on links or opening files. They are developing fileless malware that lives in memory and is harder to detect or investigate as it is wiped out when a device restarts. Finally adversaries are relying on anonymised and decentralised infrastructure, such as a Tor proxy service, to obscure command and control activities.
While Cisco has seen a striking decline in exploit kits, other traditional attacks are seeing a resurgence:
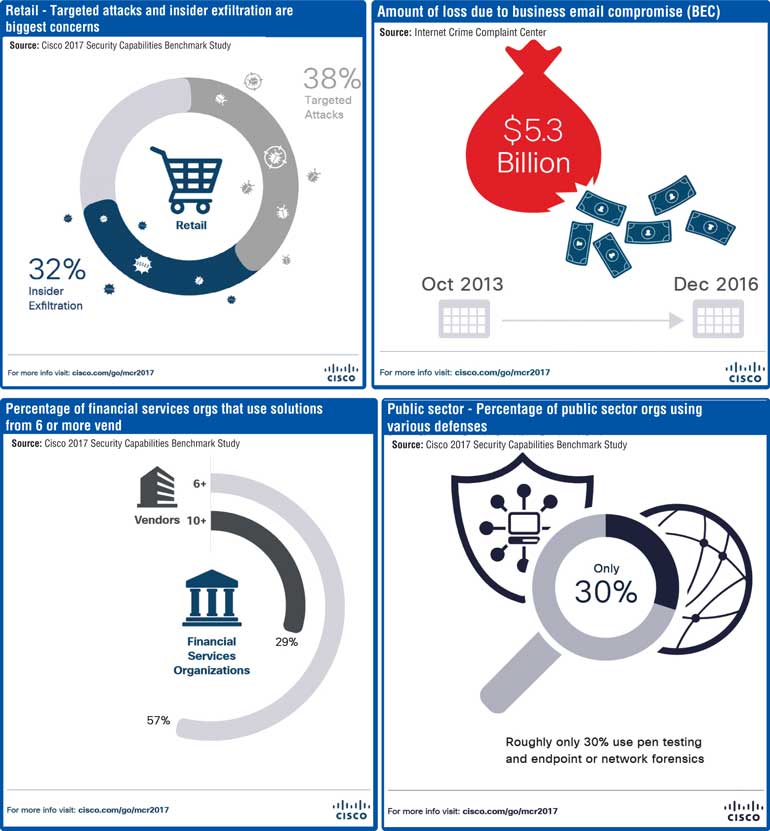
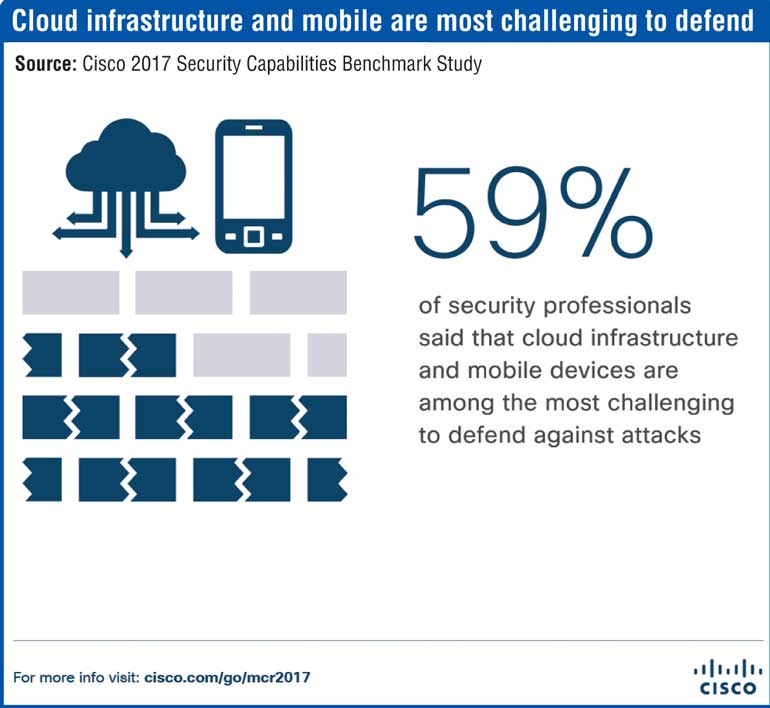
As criminals continue to increase the sophistication and intensity of attacks, businesses across industries are challenged to keep up with even foundational cybersecurity requirements. As Information Technology and Operational Technology converge in the Internet of Things, organisations struggle with visibility and complexity. As part of its Security Capabilities Benchmark Study, Cisco surveyed close to 3,000 security leaders across 13 countries and found that across industries, security teams are increasingly overwhelmed by the volume of attacks. This leads many to become more reactive in their protection efforts.
Important findings per industry include:
To combat today’s increasingly sophisticated attackers, organisations must take a proactive stance in their protection efforts. Cisco Security advises:
For the 2017 MCR, a diverse group of 10 security technology partners were invited to share data from which to jointly draw threat landscape conclusions. Partners that contributed to the report include Anomali, Flashpoint, Lumeta, Qualys, Radware, Rapid7, RSA, SAINT Corporation, Threat Connect and TrapX. Cisco’s security technology partner ecosystem is a key component of the company’s vision to bring security that is simple, open and automated to customers.
The Cisco 2017 Midyear Cybersecurity Report examines the latest threat intelligence gathered by Cisco Collective Security Intelligence. The report provides data-driven industry insights and cybersecurity trends from the first half of the year, along with actionable recommendations to improve security posture. It is based on data from a vast footprint, amounting to a daily ingest of over 40 billion points of telemetry. Cisco researchers translate intelligence into real-time protections for our products and service offerings that are immediately delivered globally to Cisco customers.
Cisco Executive Security Video with Steve Martino: Cisco 2017 Midyear Cybersecurity Report
Cisco 2017 Midyear Cybersecurity Report
Cisco Blogs: Threats with Escalating Impact: Announcing the Cisco 2017 Midyear Cybersecurity Report
Cisco 2017 Midyear Cybersecurity Report Graphics