Sunday Feb 15, 2026
Sunday Feb 15, 2026
Friday, 14 September 2018 00:00 - - {{hitsCtrl.values.hits}}
 Stop us if you’ve heard this before: avoid installing apps from outside Google Play. But what if you’re itching to battle it out in Fortnite?
Stop us if you’ve heard this before: avoid installing apps from outside Google Play. But what if you’re itching to battle it out in Fortnite?
First, a quick recap: Epic Games has decided to eschew distributing the Android version of its blockbuster game, Fortnite, via Google Play, instead making it available exclusively from its own website. Epic Games CEO Tim Sweeney has said that the move reflects the company’s goal to “bring its games directly to customers”, although he also made no bones about their motivation to avoid what he called a “bad deal” served up by PC and smartphone storefronts to game developers.
What may be in store for the security of users as a result of the move? The picture may not be pretty. In fact, the decision immediately had many in the cybersecurity community scrambling for their keyboards to warn of risks that the move – unprecedented for such a smash-hit app – may spell for its huge player base. And justifiably so, as the decision happens to play into the hands of crooks of various stripes, however unintentionally. Put bluntly, it gives a field day to scammers to take aim at millions of gamers who are too thrilled (or naïve) to look out for threats.
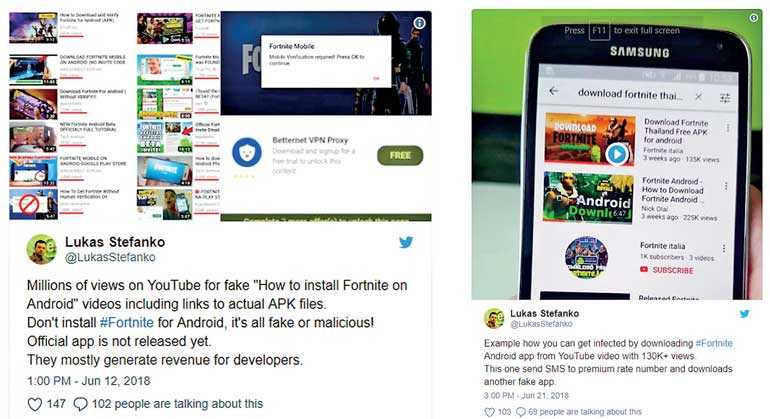
Indeed, the game had become cybercriminal catnip even before Epic Games dropped the bombshell. Malware slingers used the online shooter as a ploy to foist their harmful wares on legions of gamers months ago. ESET malware researcher Lukáš Štefanko warned players on Twitter in June about malicious knock-offs of the game that sought to capitalize on its runaway success. Frankly, scammers were never very likely to pass up the opportunity to exploit the players’ pent-up anticipation following the developer’s announcement in March that it would release the game on mobile platforms.
Fast forward to today and the heightened level of concern is justified, if for no other reason than because of Fortnite’s astounding popularity and its key audience – teens and young adults. According to its developer, the game’s player base ballooned to 125 million registered players in less than a year since it was launched.
Naturally, a large chunk of them have Android-powered devices and are keen to duke it out with other players on their smartphones or tablets.
So why worry? Well, mainly because those who wish to download Fortnite first need to allow the installation of apps from places other than Google Play, which removes a critically important – and enabled by default – security precaution on Android devices.
The main pain point, then, is that many aspiring players will skip their homework and fail to double-check the authenticity of the website from which they install the coveted game. As a result, they run the risk of ending up with one of the game’s malicious fakes instead. Not to mention the fact that even going to the legitimate source could entail an unexpected risk: a serious vulnerability in the game’s installer app, though now fixed by Epic Games, has caused further concern.
Ditching that key security precaution may spell trouble, especially for more than 8 out of every 10 Android users who run neither of the platform’s latest versions (“8.0/8.1 Oreo” and “9.0 Pie”) and can only allow app sideloading at a system-wide level. (Since Oreo, this permission has been a per-app, rather than a system-wide, option, although that still doesn’t delegitimize downloading software from outside Google Play and can be risky.)
Now, will they remember – or even care – to turn the default settings back on? That is, not just once, but every time the app asks to update itself? Could the move encourage the generally risky practice of downloading apps from places other than Google Play? Whatever the magnitude of its implications for security, the developer’s decision surely opens a can of worms, however unintentionally.
And this sends an important message to players and, often, also to their parents: once more, you need to step up your security game.
(Tomáš Foltýn is a Security Writer at ESET.)
(This article was originally featured in ESET’s welivesecurity blog.)