Tuesday Feb 17, 2026
Tuesday Feb 17, 2026
Monday, 17 December 2018 01:35 - - {{hitsCtrl.values.hits}}
By Lenard Kleinman
The pace and impact of digital transformation is no doubt accelerating and some would say, the catalyst of change. This is no different around the world including the island nation of Sri Lanka. I had the good fortune of participating in the recent 11th National Cyber Security Week 2019, organised by SL-CERT and ICTA at the Hilton Colombo. 
What is readily apparent is the nation’s progressive approach to cyber security with many achievements the envy of other nations - including being the first nation in South Asia to be admitted to the Budapest Convention.
The event was timely, following the recent release of Sri Lanka’s first National Information and Cyber Security Strategy, and it certainly looks to be a solid attempt for paving the way towards a robust national framework on enhancing cyber security. As a nation, Sri Lanka is embracing a digital future and the integration of digital technology into all areas of a business, fundamentally changes how you operate and deliver value to citizens.
As such, the singling out of the importance of critical infrastructure protection is evident throughout the document. The establishment of a new centralise authority for cyber security – the National Information and Cyber Security Agency (NICSA) and the structures under it seem well placed to develop and execute on the program in the quest to build critical infrastructure resilience. A key component to this success is the ability to understand how to merge technology with strategy and the document articulates a well thought out approach.
For myself, the emphasis on critical infrastructure security was the focus of my delivery. Of particular importance was the opportunity to learn from the events of recent past, that is the previous notable attacks on critical infrastructure.
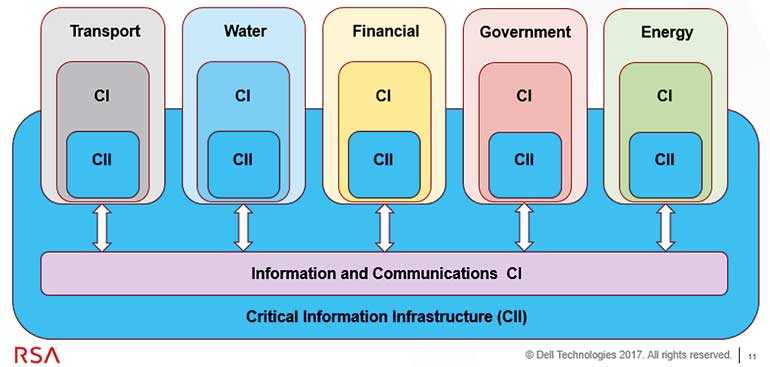
Firstly, one must be clear on what exactly we are talking about when it comes to critical infrastructure as this terms is easily thrown about. The reality is that what we in the cyber security industry are really focused on are the ‘critical Information Infrastructures’ within the critical infrastructure sector. However we also have to include the public critical information and communications infrastructures such as the satellites, mobile communications and of course, the Internet itself in this conglomerate. Together, they make up the area of concern for cyber security practitioners.
We also have to note that within the critical infrastructure sectors there are some with unique elements that cause them to stand out – I am referring of course to the control systems networks of energy generation, power distribution and the like.
There has been much said about the doom-and-gloom of critical infrastructure attacks but analysis of these previous attacks yield some sobering results:
Pretty much all of these attacks traverse the corporate IT network to get to the industrial control systems network
The methods of attack are consistent to what we have been experiencing in traditional attacks on corporate systems and environments
Poor cyber hygiene plays a large part in the success of these attacks
An important point to note is that such attacks are not about stealing credit card information, personal information or other such data elements. Instead such compromise is very much on ‘owning’ the asset. As such a successful attack on a critical infrastructure can transcend the cyber-physical realm and lead to a loss of human life. A fundamental difference to traditional cyber-attacks.
However, understanding the techniques, tactics and procedures (TTP) allows you to develop a plan of resilience based on layered defensive techniques and good cyber hygiene practices.
Some suggestions for the critical infrastructure sector of Sri Lanka are:
Employ network segmentation. Network segmentation allows you to employ zone based controls such as restricting protocols to only those needed for specific functions within a zone.
You can go further with the introduction of a demilitarized zone (DMZ) which adds an additional layer of protection and acts as a ‘proxy’ between the corporate network and the control systems network. Ensure that this is properly configured and managed.
The adding of multi-factor authentication is long overdue. For a long time now there is been a question around the security of password/passphrases from theft and the abuse of remote access for infiltration, data exfiltration, and persistence. The strategy is emphasised for remote access and for performing privileged task and actions. . In particular admin accounts should be restricted – governed by the duties, and not allowed to browse the web!
Lastly, visibility through monitoring and deep inspection. Visibility is truly the best weapon a cyber-defender has. Being able to see into the network allows you to better understand what is happening and therefore act on the traffic in the network. Not only can you address your preventive program through identification and managing behaviours but you also utilised the same technology in your investigations and remediation. Critical infrastructure network security is predicated on visibility.
RSA is a strategic principal of Just In Time Group (JIT). Founded in 1996, JIT is a veteran in the ICT Systems and Integrated Solutions sector in Sri Lanka. JIT has been recognised in the APAC CIO Outlook magazine’s Annual Top 25 Government and Public Sector Technology Providers in 2017 and was the only local company to be featured. With over two decades of excellence, JIT provides cutting-edge integrated solutions to telecommunications, government, health, defence, and financial sectors.
(Lenard Kleinman is the Chief Cyber Security Advisor and spokesperson internally and externally for RSA, Asia Pacific & Japan (APJ) focusing on Government. He has over 25 years of experience in the information technology industry, with an early focus on Oracle CASE, network operations and database administration. His current focus is to work with executives and business stakeholders to make security a strategic priority that translates into business value. Len has worked in senior roles in IT security at the Australian Tax Office, including governance and risk, compliance, and the IT Security Advisor role. In his most recent role as Senior Director of the Vulnerability Management and Research team (VMR), Len contributed to the development, implementation and review of cyber security strategy. Len is the current Branch Executive for the Canberra chapter of the Australian Information Security Association (AISA), a member of the Global Digital Infrastructure Alliance, and sits on The Harvard Group Advisory Council. He has qualifications in Information Systems, Management, Tax Administration Law and Risk Management. A security technology community activist, he is involved in and supports several cyber security and technology organisations and regularly speaks at security events.)