Monday Feb 16, 2026
Monday Feb 16, 2026
Tuesday, 12 March 2019 00:00 - - {{hitsCtrl.values.hits}}
Sri Lanka’s lack of a proper framework in anti-money laundering and counter-terrorist funding was highlighted by the European Commission in February, listing Sri Lanka among 23 countries with strategic deficiencies in their anti-money laundering and counter-terrorist financing frameworks (http://www.dailymirror.lk/article/SL-lacks-proper-frameworks-in-anti-money-laundering-counter-terrorist-funding-EU-162392.html?fbrefresh=1550241131). FIS Principal Solution Architect Jwahar Bammi shares his professional insights on how we can fight back and understand what the fight is all about
C-level bank executives surveyed in 2016 and 2017 by Bank Director magazine in its Risk Practices Survey named cyber security as their top risk concern by a long shot. More than three-quarters (77%) of respondents named this as their greatest worry, ahead of compliance (54%), credit (39%), operational issues (29%) and other common issues. It is no wonder, since cybercriminals steal more than $450 billion in money, data and IP each year.
Their tactics are diverse and insidious. Botnet attacks compromise your servers, providing criminals with access to your assets, denying service to legitimate traffic and further wreaking havoc. Account takeovers enable fraudsters to gain control of bank, credit card or email accounts so they can steal funds. Privileged user compromises, the most common tactic of all, leverage the credentials of your IT and C-suite employees – ironically, those most responsible for your company’s security. Ransomware takes over your business-critical assets and demands money, so you can regain control.
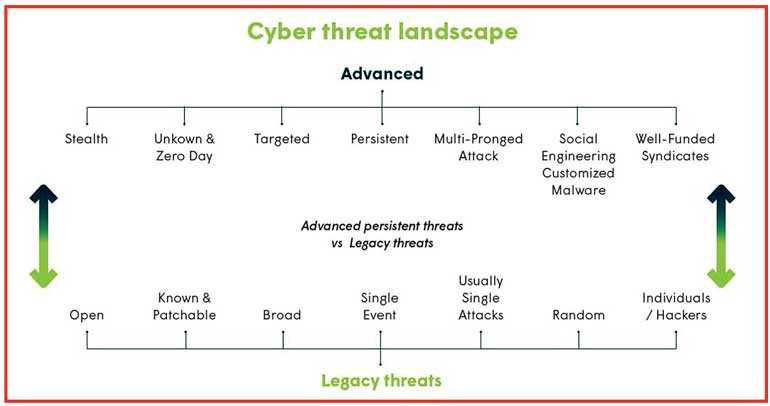
Cyberattacks continue to evolve, becoming increasingly stealthy and persistent. Once, they used to be broad, untargeted attempts by individual hackers, more easily detected and quickly patchable.
These random, single-event incidents came and went, and the experts became skilled at squelching them.
Today, however, the stealthy organised crime networks are well-funded and equipped to launch highly targeted, prolonged attacks that can go undetected for months before great damage is inflicted.
Beyond cyberattacks: All channels at risk
Indeed, cyberattacks dominate the news, but vulnerability goes far beyond internet attacks. Board directors, chief information and risk officers, and others responsible for safeguarding their companies’ data and customers can’t disregard the abundant threats in other channels – at the ATM, at the point of sale, in branches and call centres, and via mobile devices.
Further, whatever the payment type, breaches are common, whether it be mobile payments, online banking, checks, bill pay, wire, deposits, funds transfers or cash. And not all bad actors are those murky lone wolves or even the sophisticated crime rings, because many attacks are the result of the intentional or unintentional behaviour of a company’s own employees.
Compounding the challenge is the fact that suspicious behaviour from channel to channel is not the same, making it difficult to find a one-size-fits-all solution.
The tip-offs to ACH fraud don’t parallel the clues that suggest deposit fraud, kiting or on-us deception. Other indicators point to employee crime, because insiders know your operations, channel by channel, better than anyone else. A disgruntled or misguided team member can abuse their position by misusing the general ledger, stealing confidential customer information, taking over accounts, committing identity theft and performing other unauthorised actions in every channel.
The impact of financial crime on institutions
The definition of financial crime is broad, with the perpetrators disguising their activities through a confusing, complex network of multinational criminals who are laundering money and financing terrorists. While financial services providers tend to focus on check, payment card and mortgage fraud, international law enforcement authorities are equally committed to tracking down those who commit securities fraud (e.g., insider trading and market manipulation), insurance and medical fraud, tax evasion, bribery, embezzlement, identity theft, forgery, counterfeiting and more. Drug and human trafficking are often part of the equation.
The result is that financial services providers, along with providers of many other types of services, are subjected to a crushing burden of reporting requirements, even to the extent of having impossible responsibilities for tracking and mapping increasingly complex criminal relationships. In addition, institutions are faced with the challenge of rapidly executing innovation so they can stay current with the relentless changes in the payments landscape.
The costs to remain competitive and in compliance are staggering, dramatically interfering with any organisation’s efforts to focus on its core mission. To cope with the burden and address crime in all current and emerging channels, leading-edge technology is essential.
Advanced protection from financial crime
When choosing a comprehensive solution to protect your company, its data, your customers and your reputation, many considerations come into play. The key to prevention is early detection of intrusions, which is why advanced technologies continually analyse millions of records in real or near real time across data feeds from all channels.
The algorithms and business rules built into these systems enable data analytics techniques, including pattern matching, link analysis, logistic regression, cluster analysis, Bayesian probability distribution, supervised and unsupervised learning models, behaviour profiling, and the identification of peer groups and collusive networking. With this arsenal of tools, abnormal behaviour patterns are detected, triggering alerts when anomalies become evident, scoring each suspicious event into red, yellow and green categories.
Sophisticated systems leverage and localise threat intelligence from recognised entities, such as the Department of Homeland Security (DHS) and the Financial Services – Information Sharing and Analysis Centre (FS-ISAC). Because of their continual data analysis, these solutions can instantly:
An invaluable feature of forward-looking financial crime solutions is the ability to visualise the intrusion, literally, as it is occurring.
For example, IT personnel can see the progression of an account takeover attempt, starting with a graphical depiction of the account owner’s rights being breached and confidential information being accessed. This visibility provides details and linkages to hidden relationships. The unknown becomes known, and the entire cyber threat is exposed, quantified and made visible for rapid response that can prevent a massive financial disaster.
Alert management, case management and forensics
Once an anomaly is detected in any channel, by an outsider or an insider, a comprehensive financial crime prevention system will generate an instant alert. It could be an abnormality related to ACH, a case of deposit fraud, an instance of check kiting, or a counterfeiting or forgery attempt. Advanced analytics have the built-in ability to detect the unique signs that characterise wrongdoing in each channel and each transaction.
The alert goes into a centralised repository where users can gain a holistic, cross-channel view of each affected customer’s risk, and manage each alert. Priorities can be determined and, where justified, alerts can be escalated into cases. Most importantly, the crime can often be stopped before it occurs. When alerts become cases, each active investigation must be closely tracked, so it’s essential that investigators have access to data from a variety of sources. This allows them to monitor case progress, manage workflows and adhere to strict internal and external regulatory timelines. Silos between departments, business units and geographical locations cannot stand in the way, or informed decision-making will suffer.
Forensic research tools, as part of the technology built into modern financial crime prevention systems, are a critical piece of the effort to recover losses and bring the criminals to justice. The technology you choose should drive efficiency by pre-populating fields, forms and letters. Further, it should automate the electronic filing of critical documents, such as suspicious activity reports (SARs), as well as the generation of legal affidavits and customer communications. Other capabilities include the rigorous collection of accounting records and other evidence that makes it possible to present the case to a court of law for the ultimate resolution of the case.
Win the war against crime, channel by channel
The cybercriminals won’t slow down, because they have too much to gain by targeting institutions that haven’t taken adequate steps to protect their data, treasury, customer base and reputation. But while the fraudsters continue to hone their tactics, technology is just as determinedly developing ways to block their dark efforts, helping you protect the interests of all stakeholders.
(FIS is a strategic principal of Just In Time Group (JIT), a veteran in the ICT Systems and Integrated Solutions sector in Sri Lanka. JIT has been recognised in the APAC CIO Outlook magazine’s Annual Top 25 Government and Public Sector Technology Providers in 2017 and was the only local company to be featured. With over two decades of excellence, JIT provides cutting-edge integrated solutions to telecommunications, government, health, defence, and financial sectors. FIS is a global leader in financial services technology, with a focus on retail and institutional banking, payments, asset and wealth management, risk and compliance, and outsourcing solutions. Through the depth and breadth of our solutions portfolio, global capabilities and domain expertise, FIS serves more than 20,000 clients in over 130 countries. Headquartered in Jacksonville, Fla., FIS employs more than 53,000 people worldwide and holds leadership positions in payment processing, financial software and banking solutions. Providing software, services and outsourcing of the technology that empowers the financial world, FIS is a Fortune 500 company and is a member of Standard & Poor’s 500 Index.)
References: