Monday Feb 16, 2026
Monday Feb 16, 2026
Thursday, 27 February 2020 00:00 - - {{hitsCtrl.values.hits}}
By Chatura Thenuwara
Sophos, a global leader in next-generation cybersecurity, in recent research revealed the widespread use of HTTPS (Hypertext Transfer Protocol Secure) connections within malware circles, especially for communicating back to Command and Control Servers (C2). A sampling of malware analyses made over the last six months revealed that nearly one-third of malware and unwanted applications enter the enterprise network through TLS (Transport Layer Security)-encrypted flows.
 |
Dan Schiappa |
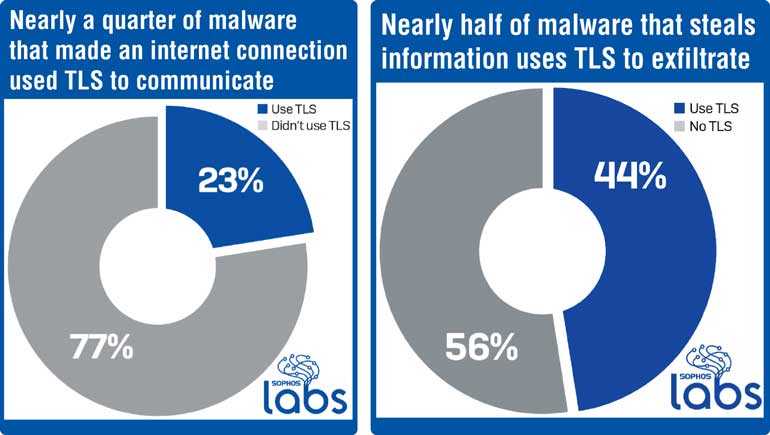
A blog titled ‘Nearly a Quarter of Malware now Communicates Using TLS’ documented, “Out of all the malware that made some kind of network connection during their infection process, about 23% communicated over HTTPS (Hypertext Transfer Protocol Secure), either to send or receive data from the C2, or during installation when they may use HTTPS to conceal the fact that they are retrieving malicious payloads or components.”
Malware that communicates via TLS-secured connections includes well-known malware families like TrickBot, IcedID and Dridex. The use of transport-layer encryption is just one of the methods for keeping the malware’s existence on compromised systems secret, but it helps it covertly download additional modules and configuration files and send the collected data to an external server.
“We’ve also observed that, increasingly, more malicious functions are being orchestrated from the command and control server, rather than implemented in the malware binary, and the C2s make decisions about what the malware should do next based on the exfiltrated data, which increases the volume of network traffic,” Luca Nagy, a researcher at Sophos pointed out. The article also states that 44% of prevalent information stealers use encryption to sneak hijacked data, including bank and financial account passwords and other sensitive credentials, out from under organisations. Furthermore, the research reveals network traffic encryption is more important for Trojans, especially information stealers.
“An information stealer’s main goal is to collect as much data about the victim as possible, including sensitive financial information, and remain undetected while doing so. Among our sample set, information stealers made up 16% of the total number of samples tested during
the period.”
The research was released in conjunction with Sophos’ latest release of the new ‘Xstream’ architecture for Sophos XG Firewall with high-performance Transport Layer Security (TLS) traffic decryption capabilities that eliminate significant security risk associated with encrypted network traffic, which is often overlooked by security teams due to performance and complexity concerns. XG Firewall now also features AI-enhanced threat analysis from SophosLabs and accelerated application performance. Speaking about the latest launch in a media release, Dan Schiappa, Chief Product Officer at Sophos said, “With the new Xstream architecture in XG Firewall, Sophos is providing critical visibility into an enormous blind spot while eliminating frustrating latency and compatibility issues with full support for the latest TLS 1.3 standard. Sophos’ internal benchmark tests have clocked a two-fold performance boost in the new XG TLS inspection engine as compared to previous XG versions. This is a game-changer.”