Friday Feb 13, 2026
Friday Feb 13, 2026
Friday, 19 May 2017 00:10 - - {{hitsCtrl.values.hits}}
 Reuters: Governments turned their attention to a possible new wave of cyber threats on Tuesday after the group that leaked U.S. hacking tools used to launch the global WannaCry “ransomware” attack warned it would release more malicious code.
Reuters: Governments turned their attention to a possible new wave of cyber threats on Tuesday after the group that leaked U.S. hacking tools used to launch the global WannaCry “ransomware” attack warned it would release more malicious code.
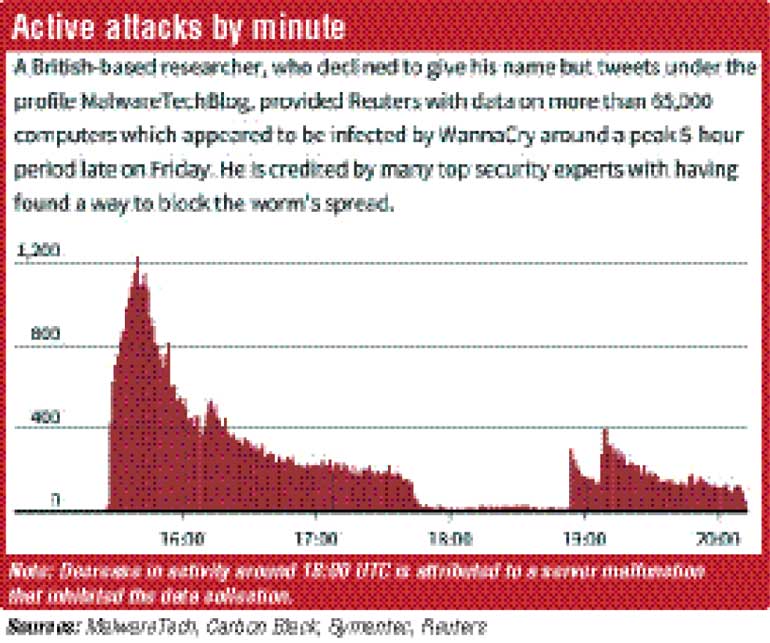
The fast-spreading cyber extortion campaign, which has infected more than 300,000 computers worldwide since Friday, eased for second day on Tuesday, but the identity and motive of its creators remain unknown.
The attack includes elements that belong to the U.S. National Security Agency and were leaked online last month.
Shadow Brokers, the group that has taken credit for that leak, threatened on Tuesday to release more recent code to enable hackers to break into the world’s most widely used computers, software and phones.
A blog post written by the group promised from June to release tools every month to anyone willing to pay for access to some of the tech world’s biggest commercial secrets.
It also threatened to dump data from banks using the SWIFT international money transfer network and from Russian, Chinese, Iranian or North Korean nuclear and missile programs. “More details in June,” it promised.
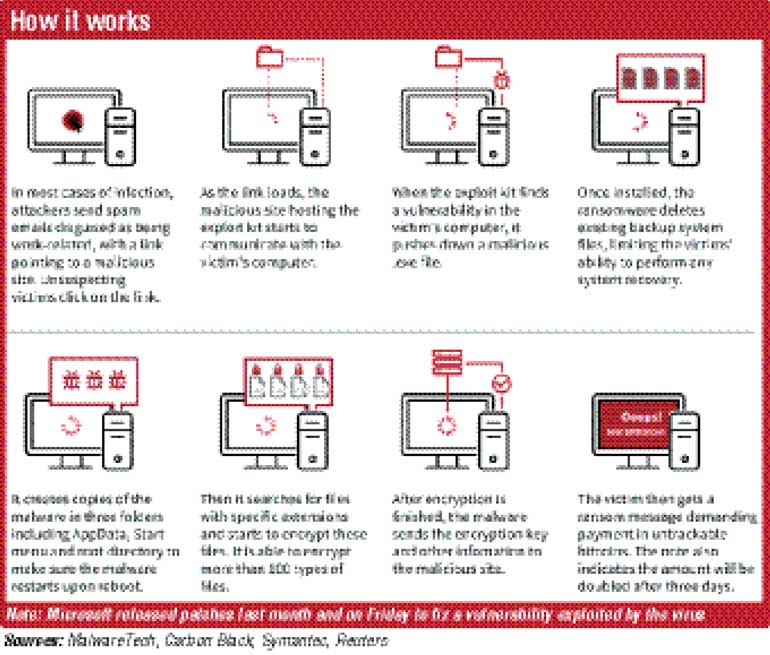
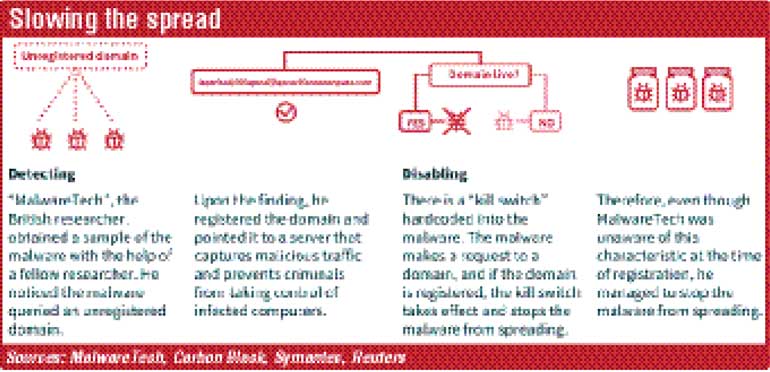
The spread of the WannaCry attack - which encrypts a user’s data and demands a “ransom” be paid electronically to free it up again - slowed to a trickle on Tuesday, with few, isolated examples being reported.
In Canada, the Universite de Montreal was hit, with 120 of the French-language university’s 8,300 computers affected, according to a university spokeswoman.
There were no new, major incidents in the United States. Fewer than 10 U.S. organizations have reported attacks to the Department of Homeland Security since Friday, a U.S. official told reporters on Tuesday.
The attack has caused most damage in Russia, Taiwan, Ukraine and India, according to Czech security firm Avast.
The United States likely avoided greater harm as the attack targeted older versions of Microsoft Corp’s Windows operating system, and more U.S. users have licensed, up-to-date, patched versions of the software, compared to other regions of the world.
The Department of Homeland Security began an “aggressive awareness campaign” to alert the tech industry to the importance of installing the patch that Microsoft issued in March that protected users from the vulnerability exploited by the attack, a U.S. official working on the attack told Reuters.
Microsoft said on Tuesday it was aware of Shadow Brokers’ most recent claim and that its security teams monitor potential threats in order to “help us prioritize and take appropriate action.”
Microsoft President and Chief Legal Officer Brad Smith said earlier this week the WannaCry attack used elements stolen from the NSA. The U.S. government has not commented directly on the matter.
No information to share
In China, foreign ministry spokeswoman Hua Chunying said she had no information to share, when asked about the origin of the attack and whether North Korea might be connected.
Several Asian countries have been affected by the malware, although the impact has not been as widespread as some had feared.
In Malaysia, cyber security firm LE Global Services said it identified 12 cases so far, including a large government-linked corporation, a government-linked investment firm and an insurance company. It did not name any of the entities.
“We may not see the real picture yet, as companies are not mandated to disclose security breaches to authorities in Malaysia,” said LE Global CEO Fong Choong Fook.
“The real situation may be serious. In one of the cases, the attack was traced back to early April.”