Sunday Feb 15, 2026
Sunday Feb 15, 2026
Monday, 15 May 2017 00:01 - - {{hitsCtrl.values.hits}}
AFP: Cyber security experts rushed to restore systems on Saturday after an unprecedented global wave of cyberattacks that struck targets ranging from Russia’s banks to British hospitals and a French carmaker’s factories.
The hunt was on for the culprits behind the assault, which was being described as the biggest cyber ransom attack ever.
State agencies and major companies around the world were left reeling by the attacks which blocked access to files and demanded ransom money, forcing them to shut down their computer systems.
“The recent attack is at an unprecedented level and will require a complex international investigation to identify the culprits,” said Europol, Europe’s policing agency.
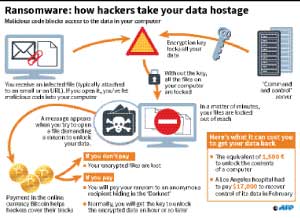
The attacks, which experts said affected dozens of countries, used a technique known as ransomware that locks users’ files unless they pay the attackers a designated sum in the virtual Bitcoin currency.
Mikko Hypponen, chief research officer at the Helsinki-based cyber security company F-Secure, told AFP that the attack was “the biggest ransomware outbreak in history”, saying that 130,000 systems in more than 100 countries had been affected.
He said that Russia and India were hit particularly hard, in large part because the older Windows XP operating software is still widely used in the countries.
The attacks apparently exploited a flaw exposed in documents leaked from the US National Security Agency (NSA).
The attacks hit a whole range of organisations and businesses worldwide.
French carmaker Renault was forced to stop production at sites in France and Slovenia, saying the measure was aimed at stopping the virus from spreading.
In the United States, package delivery group FedEx acknowledged it had been hit by malware and said it was “implementing remediation steps as quickly as possible.”
Russia’s interior ministry said that some of its computers had been hit by a “virus attack” and that efforts were underway to destroy it.
The country’s central bank said the banking system was hit, and the railway system also reported attempted breaches.
The central bank’s IT attack monitoring centre “detected mass distribution of harmful software” but no “instances of compromise”, it said.
Russia’s largest bank Sberbank said its systems “detected in time attempts to penetrate bank infrastructure”.
Germany’s Deutsche Bahn computers were also impacted, with the rail operator reporting that station display panels were affected.
Self-replicating ‘worm’
In a statement, computer security group Kaspersky Labs said it was “trying to determine whether it is possible to decrypt data locked in the attack – with the aim of developing a decryption tool as soon as possible.”
On Saturday, a cyber security researcher told AFP he had accidentally discovered a “kill switch” that could prevent the spread of the ransomware. The researcher, tweeting as @MalwareTechBlog, said that the discovery was accidental, but that registering a domain name used by the malware stops it from spreading. Computers already affected will not be helped by the solution.
But @MalwareTechBlog warned that the “crisis isn’t over” as those behind it “can always change the code and try again”.
The malware’s name is WCry, but analysts were also using variants such as WannaCry.
 Message to users: ‘Oops’
Message to users: ‘Oops’
Britain’s National Cyber Security Centre and its National Crime Agency were looking into the UK incidents, which disrupted care at National Health Service facilities, forcing ambulances to divert and hospitals to postpone operations.
Pictures on social media showed screens of NHS computers with images demanding payment of $300 (230 pounds, 275 euros) in Bitcoin, saying: “Ooops, your files have been encrypted!” It demands payment in three days or the price is doubled, and if none is received in seven days the files will be deleted, according to the screen message.
“Ransomware becomes particularly nasty when it infects institutions like hospitals, where it can put people’s lives in danger,” said Kroustek, the Avast analyst.
A hacking group called Shadow Brokers released the malware in April claiming to have discovered the flaw from the NSA, Kaspersky said. Although Microsoft released a security patch for the flaw earlier this year, many systems have yet to be updated, researchers said.
“Unlike most other attacks, this malware is spreading primarily by direct infection from machine to machine on local networks, rather than purely by email,” said Lance Cottrell, chief scientist at the US technology group Ntrepid. Some said the attacks highlighted the need for agencies like the NSA to disclose security flaws so they can be patched. G7 finance ministers meeting in Italy discussed the attacks and were expected to commit to stepping up international cooperation against a growing threat to their economies.
Computer Society of Sri Lanka (CSSL) advices users to keep their operating systems and anti-virus software updated with the latest patches and definitions. Users should also refrain from opening suspicious emails, especially if they contain attachments as well as from clicking on unknown web links. Users are also strongly advised to take complete backups of their computers as it is the easiest method of recovering files in the unfortunate event that a computer is infected.
Reuters: Malicious software called ‘ransomware’ has forced British hospitals to turn away patients and affected Spanish companies such as Telefonica as part of a global outbreak that has affected tens of thousands of computers.
What is WannaCry – also known as WanaCrypt0r 2.0, WannaCry and WCry?
How does it work?
WannaCry is a form of “ransomware” that locks up the files on your computer and encrypts them in a way that you cannot access them anymore.
How does it spread?
Ransomware is a program that gets into your computer, either by clicking on the wrong thing or downloading the wrong thing, and then it holds something you need to ransom. In the case of WannaCry, the program encrypts your files and demands payment in bitcoin in order to regain access. Security experts warn there is no guarantee that access will be granted after payment. Some ransomware that encrypts files ups the stakes after a few days, demanding more money and threatening to delete files altogether.
There are different variants of what happens: Other forms of ransomware execute programs that can lock your computer entirely, only showing a message to make payment in order to log in again. There are some that create pop-ups that are difficult or impossible to close, rendering the machine difficult or impossible to use.
Where has it spread?
British based cyber researcher Chris Doman of AlienVault said the ransomware “looks to be targeting a wide range of countries”, with initial evidence of infections in at least two dozen nations according to experts from three security firms.
The broad based ransomware attack has appeared in at least eight Asian nations, a dozen countries in Europe, Turkey and the United Arab Emirates and Argentina and appears to be sweeping around the globe, researchers said.
What is so special about WannaCry?
WannaCry is not just a ransomware program, it’s also a worm. This means that it gets into your computer and looks for other computers to try and spread itself as far and wide as possible.
Ransomware has a habit of mutating and so it changes over time in order to find different ways to access computers or to get around patches (operating system updates that often include security updates). Many security firms are already aware of WannaCry in past forms and most are looking at this one right now to see how it might be stopped.
Several cyber security firms said WannaCry exploits a vulnerability in Microsoft and that Microsoft patched this in March. People don’t always install updates and patches on their computers and so this means vulnerabilities can remain open a lot longer and make things easier for hackers to get in. It exploited a vulnerability in the Windows operating system believed to have been developed by the National Security Agency, which became public last month. It was among a large number of hacking tools and other files that a group known as the Shadow Brokers released on the Internet. Shadow Brokers said that they obtained it from a secret NSA server.
The identity of Shadow Brokers is unknown though many security experts believe the group that surfaced in 2016 is linked to the Russian government.
The NSA and Microsoft did not immediately respond to requests for comment.