Monday Feb 16, 2026
Monday Feb 16, 2026
Friday, 2 October 2015 00:00 - - {{hitsCtrl.values.hits}}


By Kiyoshi J Berman
The third annual Cyber Security Summit organised jointly by the Daily FT and CICRA Consultancies concluded successfully on Tuesday with a record participation of over 300 representatives from the private and public sector as well university students.
The main objective of the summit held at the Cinnamon Lakeside was to create awareness over the importance of cyber security and to provide top officers in the private and public sectors and IT professionals with best practices in acquiring, implementing, managing and measuring information security postures of their organisations as well as equipping them with countermeasures. The summit also highlighted the current flaws in information security that affect businesses. Discussions and presentations revolved around some of the most malicious attacks and potential threats in the security field.
The inaugural session featured new Minister of Telecommunication and Digital Infrastructure Harin Fernando as the Chief Guest and International Telecommunication Union Asia Pacific’s Senior Advisor Sameer Sharma as the Keynote speaker. Summit’s National Partner ICT Agency Managing Director Muhunthan Canagey and Central Bank Governor Arjuna Mahendran were the Guests of Honour.
The technical sessions featured top experts from CISCO and Microsoft, who were also the Strategic Partners of the Summit and several others. The full-day summit was followed by ‘Night Hack’ – an innovative and informative evening, showcasing the immediate and potential threats and dangers posed by cyber criminals today. Following are highlights from the presentations made at the technical sessions.
Threat intelligence for cyber security
Srikanta Prasad, Principal Consultant Cisco Security India delivered a presentation on ‘Threat Intelligence for Cyber Security’. Srikanta explained Cisco’s global security intelligence operation known as Talos. It has been named after a giant bronze man in Greek Mythology who protected Europa from pirates and invaders.
In the history of the mitre CVE project for the last 15 years, only 75,544 Common Vulnerabilities and Exploits have been detected. Yet we come across and average of 1.1 million malware per day and this keeps increasing. The threat landscape indicates 19.7 billion total threat blocks daily which accounts to 82 thousand virus blocks, 181 million spyware blocks and 818 million web blocks, he mentioned
Further he further explained that the multi-tiered defence is the way to address these rising threats. “Intelligence powers everything, we pull in tons of data, Intel helps consolidate and make sense of that data. Detection research then utilises that data to fuel all the security products they support. They have reverse engineers, malware analysts, domain reputation, and spam experts take that distilled data and turn it into something actionable.
“Development works on engines that help deliver our intelligence to all the platforms. Either APIs, backend engines that detect known and unknown threats, or actual infield detection engines that are deployed on platforms. They are fuelled by the intelligence and the under fire experience of the response team. The vulnerability development are the zero day hunters, they help us find new threats before the bad guys do, make sure our response teams know about them so they are covered in the products so our customers are protected, and work on new and innovated ways to help protect our customers through the development of mitigations for classes of vulnerabilities.”
Srikanta also mentioned about a few new exploit kits, their functionalities and emphasised why organisations should collaborate to share intelligence data and the part AGEIS, Talos’ partner program, takes in this effort.

Cyber security: Before it becomes an agenda
The next presentation was by Pierre Noel, the Chief Security Officer and Advisor for Microsoft in Asia spoke on the topic of ‘Cyber Security: Before it becomes an Agenda’.
“What do cyber criminals, hacktivists and terrorists have in common? They have no rules. Let’s talk about what is not working. Just because you have a very nice firewall, do you think these people will stand and attack your firewall while you watch laughing? Of course not! They will find other ways to attack you. They have no rules. If they think your security is really strong but still wants to attack you, it’s very easy. They are going to find a system administrator of the organisation then find his wife, put a girl in front of the system administrator and give a thumb drive and say put that thumb drive to the network of the organisation. That’s the way it works. As the Chief Security Officer, I should be right 100% of the time but they only have to be right one time.”
Having explained the types of malicious hackers out there and how implementing technology alone will miserably fail you, Pierre said: “I’m the Chief Security Officer but I prefer to be called the Chief Resilience Officer. My job is to make sure that no matter what attack they make we are resilient; we go back to business as quickly as possible. We have this philosophy at Microsoft called ‘Assume Breach’. We work on the assumption that the bad guys are there and will succeed which is a much safer assumption that believing that we’re protected all the time. We have a very different perspective and we do pretty well.”
“Organised crime communities are ones you should truly worry about. There is one thing you need to understand, around five or six years ago the organised crime community realised that they could get a lot of money out of cybercrime. We then saw a development inside these organised crime communities. They started recruiting people to develop vulnerabilities, to create malware, to weaponise malware and operate command and control servers. Today, it’s currently accepted that organised crime is making more money in cybercrime than in selling drugs,” he explained.
Emphasising on another current problem Pierre said, the location with the highest ransomware encounter rate in 2Q14 was Russia (0.81%), followed by Italy (0.59%) and Kazakhstan (0.55%). Unlike with many other types of malware, the distribution of ransomware has been highly concentrated geographically, with almost all ransomware encounters taking place in Europe, western Asia, North America, and Oceania. Ransomware encounters were virtually unknown in Central and South America, Africa, the Middle East, and eastern and southern Asia.

Adaptive security architecture
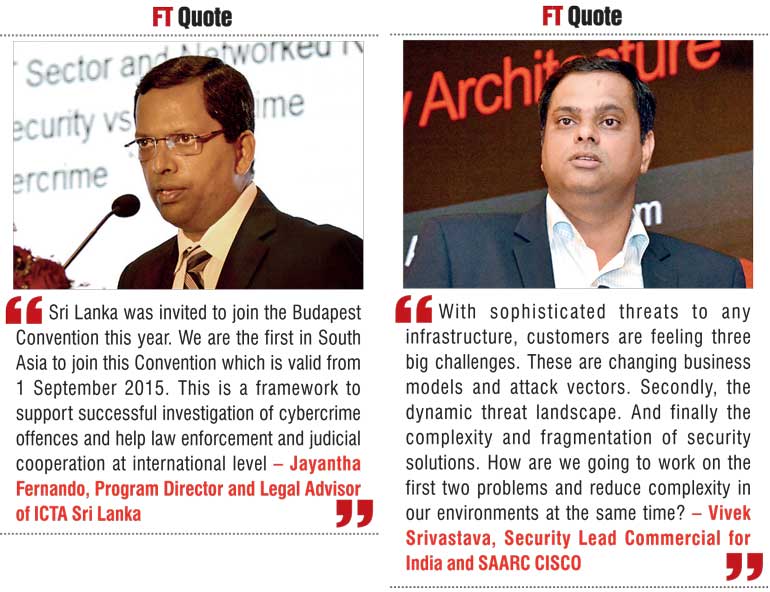
Vivek Srivastava, Security Lead Commercial for India and SAARC CISCO spoke on ‘Adaptive Security Architecture’.
“Cisco delivers intelligent cyber security for the real world, providing one of the industry’s most comprehensive advanced threat protection portfolio of solutions and services that are integrated, pervasive, continuous and open. Cisco’s threat-centric approach to security reduces complexity, while providing unmatched visibility, continuous control and advanced threat protection across the entire attack continuum, allowing customers to act smarter and more quickly – before, during, and after an attack.”
“With sophisticated threats to any infrastructure, customers are feeling three big challenges. These are, changing business models and attack vectors. How do we maintain security posture and compliance as our IT landscape when mobility, cloud, the Internet of everything – is changing? Secondly the dynamic threat landscape. How do we improve our ability to continuously protect against new attack vectors and the increasing sophistication of threats? And finally the complexity and fragmentation of security solutions. How are we going to work on the first two problems and reduce complexity in our environments at the same time? The combination of these dynamics has created security gaps, broken the security lifecycle and reduced visibility. It also creates increased complexity and management challenges,” he mentioned.
He further explained how you achieve this simplified, more holistic, more scalable model. “The answer is to focus on three strategic pillars across the entire attack continuum and ultimately your entire security system. One is to drive complete visibility, secondly insist on a laser-focus on threats, and thirdly look at how integrated platforms substantially reduce complexity while increasing your ability to scale and provide consistent control. So, why are these three areas so important?
“Being visibility driven is required because you must be able to accurately see what’s really happening in your environment to gain knowledge about your environment and threats. Visibility needs to come from the network fabric, endpoints, mobile devices, virtual environments and the cloud. The more you can see, the more you can correlate this information and apply intelligence to understand context, make better decisions, and take action – either manually or automatically. Next is to be threat focused.
“Policies and controls are important to reduce the surface area of attack, but threats still get through. You need to focus on detecting, understanding and stopping threats. With advanced malware and zero day attacks this is an on-going process that requires continuous analysis and real-time security intelligence, delivered from the cloud that is shared across all products for improved efficacy.
“You have to be platform based. Security is now more than a network issue; it requires an integrated system of agile and open platforms that cover the network, devices and the cloud. These platforms need to be extensible, built for scale and centralised management for unified policy and consistent controls. Customers will move from deploying simply point security appliances to integrating a true platform of scalable, easy to deploy services and applications.”

Impact of Budapest Cybercrime Convention on laws in Sri Lanka
Jayantha Fernando, Program Director and Legal Advisor of ICTA Sri Lanka spoke about ‘Impact of Budapest Cybercrime Convention on Laws’.
“Sri Lanka was invited to join the Budapest Convention this year. We are the first in South Asia to join this Convention which is valid from 1 September 2015. This is a framework to support successful investigation of cybercrime offences and help law enforcement and judicial cooperation at international level,” he said.
Info sec and cybercrime are inter-related; these are two sides of the same coin. Legislation covers the cybercrime areas of computer related crimes where computers used as a tool to commit other offences such as theft, cheating, misappropriation etc. Hacking that affects integrity, availability and confidentiality of a computer system or network. This also includes the spread of malware. And finally, content related cybercrime where computers with internet used to distribute illegal data such as internet-based pornography, criminal copyright infringement, he added.
The Budapest Convention is a solution to deal with legal implications of cybercrime. It’s a combination of three elements. Criminalising conduct that includes illegal access, illegal interception, data interference, system interference, misuse of devices fraud and forgery, child pornography and IPR-offences. Procedural tools for expedited preservation, search and seizure as well as interception of computer data and it enables international cooperation extradition.

Mobility and cyber security
Brian Kealey, the Country Manager for Sri Lanka and Maldives for Microsoft, delivered a presentation on ‘Mobility and Cyber Security’.
“When I think about mobility what it really means is mobility of experience. My data, my persona, my identity, all those things follow me on any device from a $ 25 Raspberry Pie to right through to another device, a large screen. The idea that I can start on one and finish it on another device. It’s about being able to work from anywhere with a connection. With that in mind, what do we do from a security and resilience perspective? We still design fortresses. We put firewalls, security devices, IDSs and secure them. But once you let people inside it’s not a fortress anymore,” he said.
He explained: “60% of the consumer electronic devices are sold in emerging markets and most of them are not built to be connected to the internet but increasingly they are. When these electronic devices are connected to the internet there are security issues. The other day when I was driving, my Apple watch vibrated and said it has an update available. So now my watch is connected to my phone and the phone is connected to the cloud. It’s going to download software from up there. Is that software reliable, secure, is the system is end-to-end to make sure it’s not trapped in my information because by the way, when you send me a text message, it comes up on my watch so it also has my data, my schedule and who I speak to. You got a huge challenge in this aspect.”
“Having said that, he pointed out that we are seeing a shift from cybercrime to cyber espionage. Countries attacking countries, warfare, and terrorism is on the rise. You think that attackers are targeting the Fortune500 but no, it’s any organisation, any small organisation. We are historically worried about malware and vulnerabilities but what we’re actually seeing now is credential theft and scams, so hacking into websites, getting people’s logins and misusing them is commonplace.”
He emphasised that these threats cannot be completely eliminated. From the Microsoft’s perspective, these issues can be addressed in three steps. First is to ruin the economic model of the attacker, second is to take away the fields we know that is to break the attack playbook and the last one is to eliminate the vectors of attack.
Angels vs. Demons: The good, bad and the ugly
The final presentation of the summit was by Krishna Rajagopal, CEO of AKATI Consulting Malaysia. Krishna’s topic ‘Angels vs. Demons: The Good, Bad and the Ugly’ was cleverly taken from two movie titles to emphasise some basic security perspectives.
“We think we are the angels, hackers are the demons. Then what happens is the hackers think, they are the angels and you’re the demon. So what happens within the organisation? The vendors think they are the angels and you’re the demon and the other way around. This is what I want to shed light on,” he said.
“There was a group selling their software called Galileo for infecting machines, intercepting communications and pretty much anything and would sell it to anybody. In Malaysia, we had four clients interestingly. We had the anti-corruption agency which is fine because they want to investigate, we had the police which is fine, then we had the Prime Minister’s department and some other company which was not even known. So the company that was not even known was spying on the other three to see who they were spying on. This was very interesting to see the original name for this company was ‘Hacking Team’ but after July 2015, we called them the Hacked Team because they were massively hacked. Every single customer that was using their product was released. This was 37 countries that were buying from them. These companies were buying exploits from underground, illegal criminals and selling it to countries. So who’s the angel and who’s the demon? Is it lawful or unlawful?
“The best part of the story was that these companies thought that this was the company which was producing these software. They didn’t know that this company was actually outsourcing the whole thing. This company called Kylax was actually creating these zero-day exploits. This is interesting because the countries don’t know about Kylax, they think the Hacking Team develops it, and Hacking Team thinks the one who developed it was Kylax themselves. But Kylax had outsourced it to underground freelancers. the part they didn’t know was that Hacking Team made a backdoor into every single customer that were 37 countries been monitored by Hacking Team while they were busy monitoring other people. This is a double trouble. In this whole equation it’s hard to say who the angel is and who the demon is,” he added.
Krishna also took findings from the famous Ashley Madison website hack to point out that cybercrime can even cause physical deaths, because in this incident four suicides had been reported. After a very entertaining session of latest exploits, Krishna concluded stating that the defence in-depth method is one powerful strategy to defend against cybercrime.
CISCO and Microsoft were the summit’s Strategic Partners while ICTA was the National Partner. The Telecommunications Partner was Sri Lanka Telecom, the Official Payment Gateway Partner was LankaPay, the Official Insurer was Continental Insurance, Official Printers were OfficeMax, LSP, the creative partner was Triad, and the Electronic Media Partners were LearnTV, TV Derana, FM Derana and Ada Derana. The Hospitality Partner was Cinnamon Lakeside.
Several leading and corporate social responsibility-savvy firms came forward to equip university students with the latest knowledge on cyber security.
The Summit saw over 50 students from Jaffna, Sabaragamuwa, Kelaniya, Sri Jayawardenepura and Colombo Universities being enriched with global and local expert presentations on cyber security threats and solutions as well as the future of the ICT industry in Sri Lanka as well as internationally.
The companies which sponsored participation of these students were CIC Holdings Plc, Citi Bank, Carson Cumberbatch Plc, Expolanka Holdings Plc, Vallibel One, Akbar Brothers, People’s Bank, HNB, Access Engineering and Pan Asia Bank.